Quantum computing is rapidly emerging as one of the most transformative technologies of the 21st century. While still in its infancy, it holds the promise of revolutionizing various fields, from material science and pharmaceuticals to finance and artificial intelligence. However, one of the most profound impacts of quantum computing is expected to be in the realm of data security and encryption. As quantum computers become more powerful, they could potentially break many of the cryptographic systems that currently protect our digital information. This article, the rise of quantum computing, will explore what quantum computing is, how it differs from classical computing, and what its rise means for data security and encryption.
Understanding Quantum Computing
What Is Quantum Computing?
Quantum computing is a type of computation that leverages the principles of quantum mechanics, a fundamental theory in physics that describes nature at the smallest scales, such as atomic and subatomic particles. Unlike classical computers, which use bits as the smallest unit of data (representing either 0 or 1), quantum computers use quantum bits, or qubits. Qubits have the unique ability to exist in multiple states simultaneously, thanks to the quantum phenomena of superposition and entanglement.
Superposition allows a qubit to be in a state of 0, 1, or any combination of both at the same time, which enables quantum computers to process a vast number of possibilities simultaneously. Entanglement is another quantum phenomenon where the state of one qubit is directly related to the state of another, no matter how far apart they are. This property allows quantum computers to perform complex calculations much faster than classical computers.
How Quantum Computing Differs from Classical Computing
The fundamental difference between quantum and classical computing lies in the way they process information. Classical computers process information in a linear fashion, evaluating one state at a time. In contrast, quantum computers can evaluate multiple states simultaneously, allowing them to solve complex problems that would take classical computers an impractical amount of time to solve.
For example, while a classical computer might take thousands of years to factorize a large number (a task critical to breaking many encryption algorithms), a quantum computer could theoretically do it in a matter of seconds using an algorithm like Shor’s algorithm. This exponential increase in processing power is what makes quantum computing so revolutionary—and so potentially disruptive to current encryption methods.
The Impact of Quantum Computing on Data Security
The Threat to Current Encryption Methods
Most of the data security systems we rely on today, including those used for online banking, email communication, and secure transactions, are based on cryptographic algorithms that are difficult for classical computers to break. These include public-key cryptography methods like RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography), which rely on the computational difficulty of factoring large numbers or solving discrete logarithm problems.
However, quantum computers have the potential to break these encryption methods. Shor’s algorithm, for example, could allow a quantum computer to factorize large numbers exponentially faster than the best-known classical algorithms. This would render RSA and similar cryptographic systems insecure, putting vast amounts of sensitive data at risk.
Post-Quantum Cryptography
In response to the threat posed by quantum computing, researchers are developing new cryptographic methods known as post-quantum cryptography (PQC). These methods are designed to be secure against both classical and quantum computers. Unlike RSA or ECC, post-quantum cryptographic algorithms are based on problems that are believed to be hard for quantum computers to solve.

The National Institute of Standards and Technology (NIST) is currently in the process of standardizing post-quantum cryptographic algorithms. NIST’s Post-Quantum Cryptography Standardization project aims to develop and evaluate cryptographic algorithms that can withstand quantum attacks. The project has already made significant progress, and the first standards are expected to be finalized in the coming years. You can learn more about NIST’s Post-Quantum Cryptography project here.
Quantum Key Distribution (QKD)
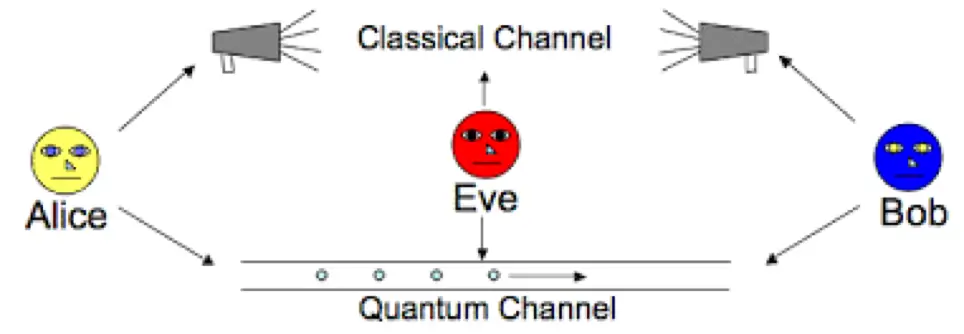
Another approach to securing data in the quantum era is Quantum Key Distribution (QKD). QKD leverages the principles of quantum mechanics to securely distribute encryption keys between two parties. The security of QKD is based on the fundamental principles of quantum mechanics, which state that observing a quantum system inherently alters its state. This means that any attempt to eavesdrop on the key distribution would be immediately detectable.
QKD has already been successfully implemented in various experimental settings and is considered one of the most promising technologies for securing communications in the quantum era. However, it is important to note that while QKD can secure the distribution of encryption keys, it does not solve the problem of quantum computers potentially breaking the encryption algorithms themselves.
Preparing for a Post-Quantum World
The Timeline for Quantum Computing
While quantum computing holds enormous potential, it is still in the early stages of development. Building a fully functional quantum computer that can outperform classical computers on practical tasks (known as quantum supremacy) is a significant scientific and engineering challenge. Current quantum computers are primarily research tools, and their capabilities are limited by issues such as qubit coherence and error rates.
However, progress in the field is accelerating. Companies like IBM, Google, and Microsoft, as well as research institutions and governments around the world, are investing heavily in quantum computing research. Google made headlines in 2019 when it claimed to have achieved quantum supremacy by performing a calculation on a quantum computer in seconds that would have taken a classical supercomputer thousands of years. Although the practical impact of this achievement is still debated, it underscores the rapid advancements being made in the field.
Given the current pace of development, experts predict that quantum computers capable of breaking current encryption methods could become a reality within the next decade or two. This means that organizations need to start preparing now to ensure their data remains secure in a post-quantum world.
Steps Organizations Can Take Today
- Stay Informed: Keeping up with developments in quantum computing and post-quantum cryptography is essential for organizations that want to protect their data in the future. This includes following research, attending conferences, and engaging with the cybersecurity community.
- Assess Risks: Organizations should assess their current cryptographic systems and determine which systems would be vulnerable to quantum attacks. This involves identifying which encryption methods are used and where sensitive data is stored and transmitted.
- Develop a Transition Plan: Organizations should begin planning for the transition to post-quantum cryptography. This includes evaluating potential post-quantum algorithms, testing them in controlled environments, and developing a roadmap for implementation once the standards are finalized.
- Invest in QKD: For organizations that require the highest level of security, investing in Quantum Key Distribution (QKD) technologies could provide an additional layer of protection. While QKD is still in the early stages of deployment, it is worth exploring for highly sensitive applications.
- Collaborate with Partners: Cybersecurity is a collective effort. Organizations should collaborate with industry partners, governments, and academic institutions to share knowledge, resources, and strategies for dealing with the quantum threat.
Ethical and Societal Implications of Quantum Computing
Balancing Innovation and Security
The rise of quantum computing brings not only technical challenges but also ethical and societal implications. As with any powerful technology, quantum computing has the potential to be used for both good and ill. On one hand, it could lead to breakthroughs in medicine, materials science, and artificial intelligence that benefit society as a whole. On the other hand, it could also be weaponized by bad actors to undermine security and privacy.
This dual-use nature of quantum computing raises important questions about how the technology should be developed, regulated, and controlled. Ensuring that quantum computing is used responsibly will require collaboration between governments, the private sector, and the academic community. It will also require transparency and accountability in how quantum technologies are deployed.
The Digital Divide in the Quantum Era
Another consideration is the potential for a digital divide in the quantum era. Quantum computing is a resource-intensive technology that requires significant investment in infrastructure, research, and talent. As a result, there is a risk that only a few wealthy nations and corporations will have access to quantum capabilities, while others are left behind. This could exacerbate existing inequalities and create new geopolitical tensions. To mitigate this risk, it is important for governments and international organizations to promote equitable access to quantum technologies. This could involve initiatives to support quantum research in developing countries, as well as efforts to share knowledge and resources across borders.
Conclusion: Embracing the Quantum Future
Quantum computing represents one of the most exciting frontiers in technology, with the potential to transform industries and solve problems that are currently beyond our reach. However, with this potential comes significant challenges, particularly in the realm of data security and encryption. As quantum computers become more powerful, they could render many of the cryptographic systems we rely on today obsolete, putting sensitive data at risk.
To prepare for this quantum future, organizations must stay informed, assess their risks, and begin planning for the transition to post-quantum cryptography. They should also explore emerging technologies like Quantum Key Distribution (QKD) and collaborate with partners to ensure that their data remains secure.

At the same time, it is important to consider the broader ethical and societal implications of quantum computing. By promoting responsible development and equitable access to quantum technologies, we can harness the power of quantum computing for the benefit of all while mitigating the risks it poses.
For more information on quantum computing and its implications for data security, you can visit these resources:






