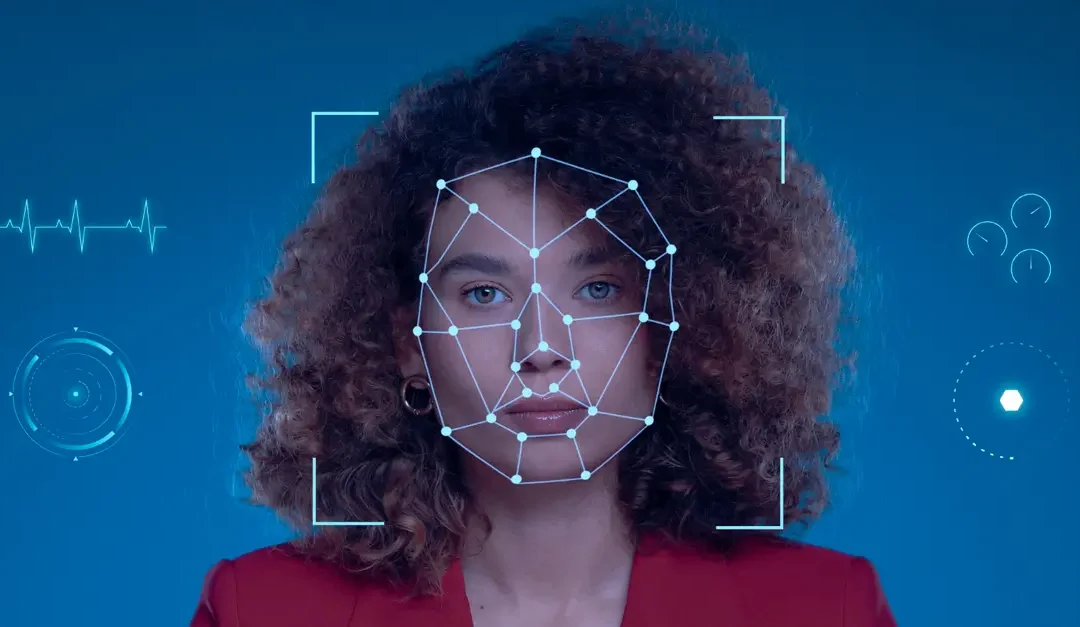
The realm of biometric technology has truly transformed the landscape of identity authentication and verification. By harnessing distinctive biological characteristics like fingerprints, facial recognition, and iris scans, we now possess more streamlined and fortified methods to access our devices, accounts, and sensitive data.
Uses of Biometric Technology
Illustratively, the incorporation of fingerprint sensors in smartphones has rendered the process of unlocking devices effortlessly seamless. Users are relieved of the burden of memorizing intricate passwords or fretting over unauthorized entry, as their unique fingerprint acts as the gateway to their personal information.
For instance, consider a scenario where a busy professional is rushing to catch a flight and needs quick access to their boarding pass on their smartphone. With a simple touch of their finger, the phone unlocks, granting them immediate access to their travel documents without the hassle of typing in a password.

Biometric Technology Safety
Nonetheless, as we embrace these technological advancements, it is imperative to carefully weigh the equilibrium between convenience and security. While biometric authentication presents a smoother user experience, it concurrently raises apprehensions regarding privacy, data security, and potential vulnerabilities.
One pivotal challenge lies in ensuring the secure storage and management of biometric data to avert unauthorized access and misuse. Organizations must institute stringent security protocols, such as encryption and multi-factor authentication, to shield this sensitive data and mitigate the perils of cyber intrusions.
For example, in the banking sector, biometric data like fingerprint scans are used to authenticate customers for financial transactions. Banks invest heavily in robust security measures to protect this data from falling into the wrong hands, ensuring that customers can conduct their transactions securely and with peace of mind.
Furthermore, the integration of facial recognition technology in airports for passport authentication epitomizes the convenience of biometrics in fortifying travel security and expediting processes. By simply gazing into a camera, travelers can hasten the boarding procedures while upholding a heightened level of identity validation.

Imagine a crowded airport where passengers are swiftly moving through security checkpoints. With facial recognition technology in place, the boarding process becomes more efficient, reducing wait times and enhancing overall travel experience for passengers.
Ethics in Biometric Technology
Another crucial aspect to contemplate is the ethical ramifications of employing biometric technology, encompassing concerns related to consent, transparency, and discrimination. It is imperative for developers and enterprises to adhere to ethical guidelines and exemplary practices to ensure the responsible and equitable deployment of biometric systems.
For instance, consider the deployment of biometric attendance systems in workplaces. While these systems offer convenience in tracking employee attendance, ethical considerations arise in terms of employee consent and data privacy. Companies must prioritize transparency and consent to uphold the ethical standards of using biometric technology in the workplace.
For instance, the incorporation of facial recognition in law enforcement necessitates meticulous attention to privacy statutes and civil liberties to forestall potential abuses of authority. Striking a harmonious balance between security imperatives and individual rights is paramount in upholding public trust and confidence in such systems.
Conclusion
In essence, while biometric technology proffers myriad advantages in terms of convenience and security, it is imperative to approach its implementation judiciously and ethically. By striking a harmonious balance between these dual facets, we can harness the full potential of biometrics while safeguarding the privacy and rights of individuals.